Worried that your cookie filenames have changed to incomprehensible random strings of letters and numbers? No need. Microsoft has, for security reasons, changed the way IE cookies are named. This is to improve security and reduce "cookiejacking", addressing one way in which attackers might be able to access your cookies (which could include your login information etc).
Side effects: some apps depending on the old cookies names system broke, eg CCleaner and WinPatrol. Also, it's now harder for users to figure out which cookies were set by which websites, as you can't tell the website name from the cookie name anymore. You have to open up the cookie file to check.
However, other browsers like Firefox aren't affected by the change - it's Internet Explorer only.
Old cookie names structure
Internet Explorer cookies used to have filenames with the structure: yourcomputerloginname@partialdomainname.txt eg johnsmith@microsoft.txt (or johnsmith@msdn.microsoft[2].txt etc).
IE cookies are typically located in your AppData\Roaming\Microsoft\Windows\Cookies folder (to find the AppData folder, click Start, in the search box type "appdata" without the quotes and hit Enter. If that doesn't work try "%AppData%" again without the quotes which may go straight to the "Roaming" subfolder).
The security hole, and update
However, in August Microsoft released a Cumulative Security Update for Internet Explorer (2559049) which (according to Microsoft Security Bulletin MS11-057) addresses a "Drag and Drop Information Disclosure Vulnerability CVE-2011-2383" which existed because IE (all versions) didn't properly restrict access to store cookie files.
In more detail for the techies, before the update Internet Explorer did not "properly restrict cross-zone drag-and-drop actions, which allows user-assisted remote attackers to read cookie files via vectors involving an IFRAME element with a SRC attribute containing an http: URL that redirects to a file: URL, as demonstrated by a Facebook game, related to a "cookiejacking" issue".
This vulnerability meant that "An attacker who exploited the vulnerability when a user views a Web page and performs a drag-and-drop operation could gain access to cookie files stored in the local machine."
What the security fix changes
To fix the vulnerability, this update modified how Internet Explorer accesses locally stored cookies, and how it manages cookie files. These changes included changing how Internet Explorer sets file names for cookies, to help make cookie file names less predictable.
Reportedly this change has been seen in several Windows operating systems, ie XP, Vista and Windows 7, and several versions of Internet Explorer including IE8 and IE9 (which would make sense as Microsoft's info says the vulnerability affects Internet Explorer 9 and previous versions).
A Microsoft blog explained the change - see the "Cookie Filenames are Randomized" heading. It's now harder for attackers to guess the location of a particular cookie as IE cookie files are now named "using a randomly-generated alphanumeric string. Cookies are not instantly renamed on [the security] upgrade, but are instead renamed as soon as any update to the cookie’s data occurs."
Consequences of the cookie name change
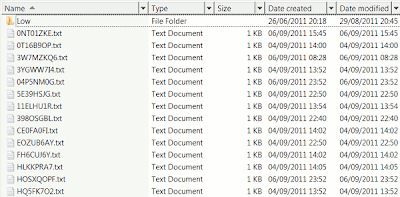
Now, cookie names look like this:
As mentioned earlier, certain software depending on the old system doesn't work anymore, and will have to be tweaked.
From the viewpoint of those protective of their privacy, while you can't see the website's name from looking at the cookie filename, you can still see it if you open up the cookie in Notepad or other text editor.
For example, here's the contents of cookies saved by Microsoft when I visited and then re-visited their webpage about the cookie change. You can see "microsoft" in there:
And here's the contents of a cookie saved by Google when I searched for info on the cookie change using the search box in Internet Explorer. Again, you can see "google.com" in there, although the filename is now "25Z1H29G.txt", and no longer mylogin@google.txt:
For more details of how it seems to work behind the scenes, I've done a separate blog post on how to view the contents of your Internet Explorer cookies in a more user-friendly way.




1 comment:
No need for paranoia on this one. Check out the site below for a full explanation, plus the workarounds that all cookie-managment apps will impliment shortly to restore all normal functionality.
http://blogs.msdn.com/b/ieinternals/archive/2011/08/12/internet-explorer-9.0.2-update-changes-file-protocol-and-cookie-naming.aspx
Post a Comment