We all know that password choice, although notoriously tricky, is vital for online or offline computer security. Longer passwords, indeed whole phrases not just words, are better against brute force attacks. Using varied types of characters should help make passwords stronger, ie mixing letters, numbers and symbols. There are tools like passphrase generators too.
So someone please, please tell me, what on earth was Barclays thinking when it came up with the following requirements for Barclaycard customers' "memorable word"? Yes I know it's not a password, but it's similar.
Note the length limitation - only 8 letters max - and you have to count them too to make sure you have more than 6. They positively ban the use of numbers / digits and symbols. (It doesn't say numbers are banned, but they are - I tried).
No consecutive letters allowed means that if you wanted to use, say "Absalom", that would be disallowed, although my main beef is that the fact that even 2 consecutive letters aren't possible is not at all clear from Barclays' example. "Absalom" won't be permitted because it contains an "a" and a "b", in a row. So customers can go mad trying to think of words that will work. Forget words that contain "de", for instance. Abd nothing Afghanistan-like allowed, not to mention Klingon-related! Now, that's not having a calming effect on customers, is it?
As for forbidding the use of the same character more than once in a row, it's well known to those interested in password security that the first word below is more secure, as well as more memorable, than the second:
D0g.....................
PrXyc.N(n4k77#L!eVdAfp9
Barclays also require users to remember a code - and it's numbers only, and limited to 6 characters. Another frustrated customer has blogged about the whole range of difficulties thrown up; take a look for more hair-tearing requirements. If we had to jump through any more hoops we'd be hulaing. Or something.
Perhaps financial institutions think that as long as requiring several tokens / items or questions is good enough to protect them (though not necessarily customers), that'll do - however hard it may be for customers to think up or remember them. In the USA, apparently requiring passwords and a few security questions may be considered to constitute adequate security measures for banks to take.
Now, Barclays say they want their online banking to be "user-friendly", and they've tried to take other steps on the security front, but really, this is ridiculous. It seems to be exactly the sort of thing security expert Bruce Schneier calls "security theatre" - stuff to make customers and others think they care about security and are taking decent security measures, when actually they're not necessarily doing that. As legal expert Nicholas Bohm and others have repeatedly argued, things won't improve unless the banks and others who control the infrastructure and systems truly bear the risk of security breaches or fraud, instead of being able to (as currently) offload the risk onto customers and merchants.
As for Barclays' "anti-fraud" technology, whoever devised their algorithm should - well I'm too polite to say what, but you get the drift. For instance, for a particular subscription, I have a regular monthly debit to my credit card, same amount, same payee. Every month. Why on earth should that transaction suddenly be thought suspicious one day, when it hasn't been for the LAST X MONTHS!!? I buy stuff from Amazon regularly, so what's wrong with that? Why should Barclays query it?
And what about extremely busy people who only have time to go shopping once in a while, and buy lots of stuff in one day in the Boxing Day sales - ooh, that's 2 pairs of shoes, a coat and 3 tops all bought all on the same day, that's not "normal", let's just nuke 'em all! And then, the icing on the cake, it blocks all transactions on the card automatically, so if you'd tried to pay a bill just before its deadline, tough luck, Barclays may now have made you overdue.
But back to passwords. Lest you think this rant is directed too much at just one target, let me finish with this example from UK government websites, from a few months back.
Businesslink - no symbols allowed.
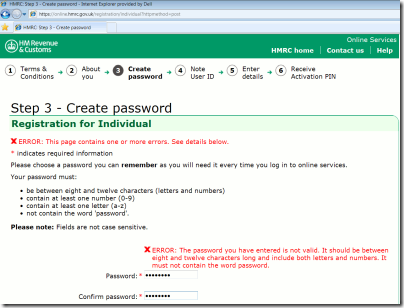
HM Revenue & Customs, yep the good ol' taxman - password limited to 12 characters only.
Sites like these should know better, one might think. I'm not sure what it would take to get the message across. If a user's account is compromised because their password was too easy to guess due to the length/symbol etc limitations, who's going to carry the can?


No comments:
Post a Comment